Security specialists have noticed an expansion in the quantity of hardware tainted with TrueBot malware downloader created by Quietness, a Russian-talking hacking bunch.
The Quietness bunch is notable for massive scope heists against monetary establishments. It all started to create some distance from phishing as a fundamental trade-off vector. TrueBot malware is utilized by Clop ransomware to acquire network access.
The noxious entertainers likewise utilize Magical transport, a recently planned information exfiltration instrument. Quiet’s assaults as of late have uncovered that the pack used Clop ransomware. The TA505 programmers subsidiary with the FIN11 bunch regularly utilizes.
Truebot infections
Quietness programmers have invaded north of 1,500 frameworks overall to get shellcode, Cobalt Strike guides, the Elegance malware, the Magically transport exfiltration device, and the Clop ransomware.
Cisco Talos specialists noticed various new cyberattacks to be utilized since August 2022 and investigated the new missions.
After taking advantage of an essential weakness in Netwrix Reviewer servers, followed by CVE-2022-31199. The assailant contaminated frameworks with Truebot (Silence.Downloader) in a few assaults in August and September. TrueBot malware is utilized by Clop ransomware to acquire network access.
The gathering changed to the utilization of USB drives to introduce malware with Raspberry Robin worm, which every now and again conveyed IcedID, Honey bee, and Truebot payloads in October 2022.
In an October report, Microsoft connected the worm to the dissemination of Clop ransomware by a danger entertainer known as DEV-0950, whose dubious assault interlinks with those of FIN11 and TA505 (known for involving Clop in coercion assaults).
As per Cisco Talos, the Truebot pack utilized Raspberry Robin to attack north of 1,000 hosts, a considerable lot of which were PCs not open through the public web, essentially in Mexico, Brazil, and Pakistan.
In November, the programmers designated Windows servers, uncovering SMB, RDP, and WinRM administrations to the public web. The specialists counted north of 500 diseases, with generally 75% of them happening in the US.
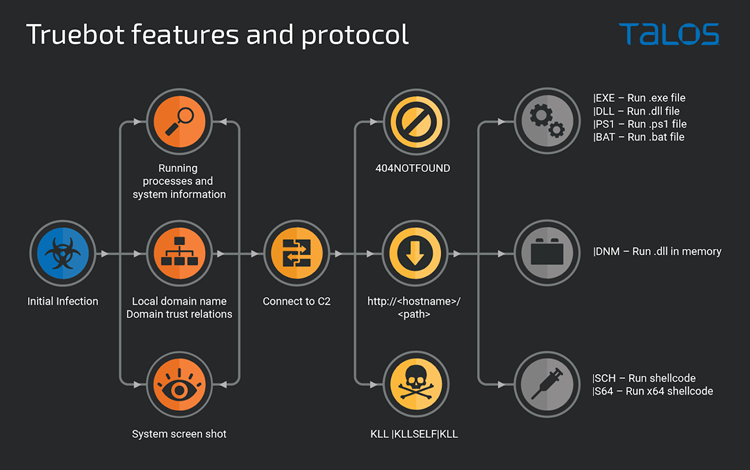
Truebot is an underlying module fit for social affairs essential data and taking screen captures. It additionally takes Dynamic Catalog trust associations data, which helps the danger entertainer in post-contamination arranging.
Truebot can then be told by the order and control (C2) server to stack shellcode or DLLs into memory, begin executing extra modules, eliminate itself, or introduce DLLs, EXEs, BATs, and PS1 documents.
New Magically transport information exfiltration instrument.
The programmers use Truebot in the post-compromise stage to drop Cobalt Strike signals or the Elegance malware (FlawedGrace, GraceWire). It has been connected to the TA505 cybercriminal bunch.
The gatecrashers then use Magically transport, of the sort that Cisco portrays as an original uniquely made device worked in C++ that permits programmers to undetectably take the information.
Magically transport’s correspondence channel with the C2 server is encoded. The professionals can restrict the posting speed, channel records in view of size, or erase the payload. This is all finished to keep a position of safety simply on the casualty’s PC.
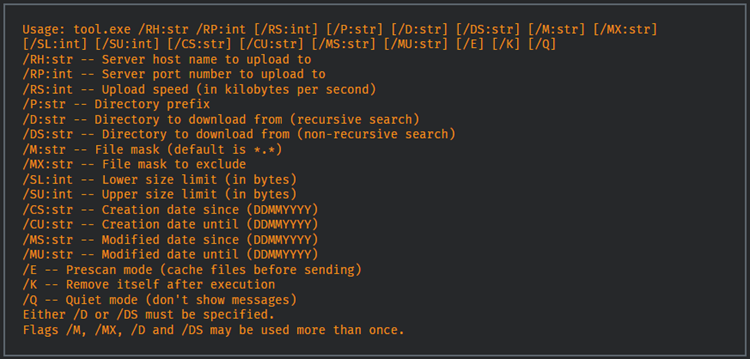
Magically transport additionally incorporates choices for taking records from OneDrive envelopes. Gathering the casualty’s Viewpoint messages, and zeroing in on unambiguous document expansions.
Now and again, the attackers use Cobalt Strike to move along the side to however many frameworks as could be expected under the circumstances prior to sending the Clop ransomware.
“During the investigation and parallel development stages,” Cisco Talos specialists make sense of, “the attackers perused key server and PC record frameworks, connected to data set frameworks and accumulated data that was marketed. The market is utilizing the Magically transport apparatus to an assaulter server.”
“When enough information was accumulated, the aggressors set up everyday obligations on an enormous number of PCs to start achieving the Clop malware and scrambling however much information as could reasonably be expected.”
Silence gang activity
Scientists at network protection firm Gathering IB have been following Quietness/Truebot activity starting around 2016 when the programmers broke into a bank but couldn’t take cash because of an installment request issue.
The assailant got back to a similar objective and started checking the monetary establishment administrator’s movement. They take screen captures and video web-based from the tainted framework to know cash move process functions.
As per Gathering IB, they committed their most memorable effective burglary in 2017. They attacked ATM frameworks and attempted to take more than $100,000 in one evening.
Quiet proceeded with their assaults, taking somewhere around $4.2 million from monetary foundations in the Soviet Association. It also includes Europe, Latin America, and Asia somewhere in the range of 2016 and 2019.
Scientists from Gathering IB depict Quietness programmers as profoundly gifted, ready to upset engineer malware to adjust this for their motivations. They also tried to adjust an adventure utilized among country state bunch Extravagant Bear at the constructing agent directions level. They can likewise make their own apparatuses.
At first, the aggressor just designated associations in Russia. However, Quiet has extended their arrival all around the world lately.





