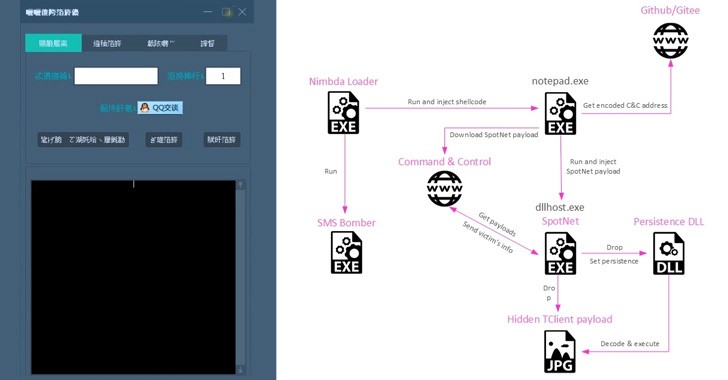
As part of a recently revealed effort, a threat cluster connected to the hacking organisation Tropic Trooper has been seen employing previously unknown malware written in the Nim programming language to attack targets.
According to a study from the Israeli cybersecurity firm Check Point, the new loader, known as Nimbda, is “bundled with a Chinese language greyware ‘SMS Bomber’ malware that is most certainly being spread illegally across the Chinese-speaking web.”
The researchers claimed that whomever created the Nim loader paid particular attention to giving it the same executable icon as the SMS Bomber that it drops and executes. The entire bundle therefore functions as a trojanized binary.
A user can enter a phone number (not their own) into SMS Bomber, as the name suggests, to flood the victim’s cellphone with messages and possibly make it unusable in a denial-of-service (DoS) attack.
The fact that the malware functions as both an SMS Bomber and a backdoor shows that the attacks are highly targeted in addition to being directed towards tool users, who are considered to be a “very unorthodox target.”
Tropic Trooper, also known as Earth Centaur, KeyBoy, and Pirate Panda, has a history of attacking targets in Taiwan, Hong Kong, and the Philippines, mostly concentrating on the high-tech, medical, and transportation sectors.
Last year, Trend Micro described the Chinese-speaking collective as “particularly sophisticated and well-equipped,” highlighting the group’s capacity to adapt its TTPs to remain undetected and rely on a wide variety of proprietary tools to compromise its targets.
The most recent attack chain identified by Check Point starts with the modified SMS Bomber tool, the Nimbda loader, which simultaneously launches an embedded executable—in this case, the genuine SMS bomber payload—and injects a separate piece of shellcode into a notepad.exe process.
This starts a three-tier infection process that involves downloading a subsequent programme from an obscured IP address listed in a markdown file (called “EULA.md”) that is housed in an attacker-controlled GitHub or Gitee repository.
The recovered binary is an improved version of the Yahoyah trojan, which is made to gather details about nearby local wireless networks as well as other system metadata and exfiltrate them back to a command-and-control (C2) server.
For its part, Yahoyah also serves as a conduit to obtain the advanced malware, which is downloaded from the C2 server as an image. The backdoor known as TClient, which was used by the gang in earlier campaigns, is the steganographically encoded payload.
The researchers came to the conclusion that “the observed activity cluster portrays a picture of a focused, determined actor with a definite aim in mind.”
The selection of a “SMS Bomber” tool for this purpose is unsettling and tells a whole story the moment one dares to extrapolate a motive and an intended victim. “Typically, when third-party benign (or benign-appearing) tools are hand-picked to be inserted into an infection chain, they are chosen to be the least conspicuous possible.”
Reference: https://thehackernews.com/2022/06/chinese-hackers-distributing-sms-bomber.html?&web_view=true





