The DAIXIN Team, a new ransomware and data exfiltration gang that has been focusing on US healthcare, has been the subject of a joint alert from the FBI, Cybersecurity and Infrastructure Security Agency (CISA), and the Department of Health and Human Services (HHS).
The DAIXIN Team was first discovered in June 2022, but after carrying out many ransomware attacks against businesses in the health and public health sectors, it swiftly caught the attention of the government. These days, it’s typical practice for ransomware operations to entail both data theft and server encryption. In this instance, the data contained both PHI and personally-identifying information (PII) about the patients.
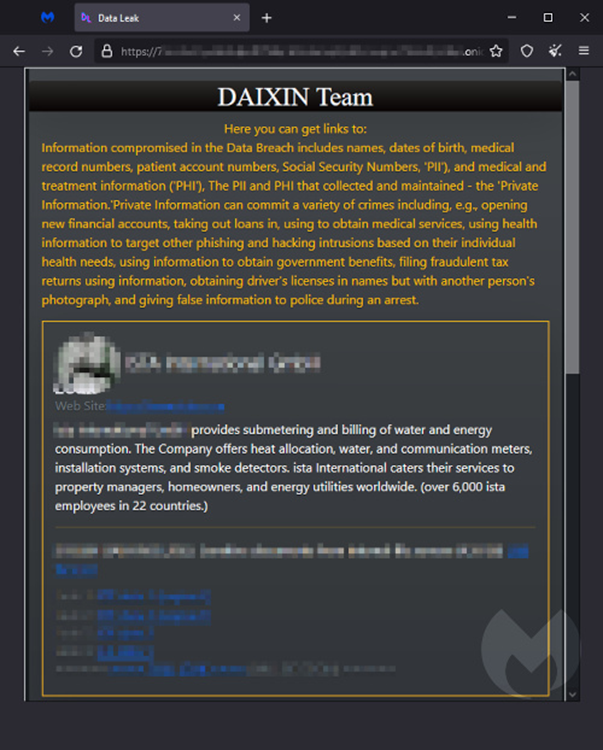
The DAIXIN leak site
According to the advice, DAIXIN Team has observed initially accessing victims’ PCs using their VPN servers. In one instance, they leveraged an unpatched vulnerability to get access to the victim, while in another, they used credentials that had been phished.
Following a successful penetration, the team does reconnaissance, elevates privileges using credential dumping or the pass-the-hash technique, collects confidential information, and releases ransomware built using Babuk Locker source code that was stolen in 2021.
Ransomware specialist Marcelo Rivero, a Malware Intelligence Analyst with Malwarebytes, claims that DAIXIN Team has recently been less active. They currently seem to have taken a break, as they haven’t added any new victims to their list this month.
If the victim doesn’t pay the ransom, the DAIXIN team publishes their personal information and releases their stolen data, as is typical of other ransomware gangs. After releasing the information on three victims in August, it only released one in September, and there haven’t been any as of yet in October, even though November is quickly approaching. The lack of published victims can be a sign of inactivity, or it might mean that the DAIXIN Team was successful in convincing victims to make payments.
However, healthcare organizations must pay attention to the warnings issued by the FBI, CISA, and HHS. In 2021, the FBI Internet Crime Complaint Center received 649 ransomware incidents, and according to their report, 148 of those reports came from the healthcare and public health industry. Despite becoming the newest ransomware threat, DAIXIN Team
Mitigations to DAIXIN
Simple mitigations can close the vulnerabilities that ransomware gangs prey upon:
- Make a strategy for timely software patching.
- Users should report phishing efforts and questionable emails.
- Require VPNs and remote desktops to use two-factor authentication (2FA).
- To find and stop ransomware, use endpoint security software with EDR.
- Using the least privilege principle, distribute access rights.
- Create network segments to make lateral mobility more challenging.
- Make and test secure, off-site backups that are not accessible to hackers.
Visit this AA22-294A alert page for more details on how to safeguard your business from DAIXIN Team and other ransomware gangs.





