Most of the thousands of hacked computers are found in Iran, the United States, Indonesia, and India, thanks to the sophisticated botnet MyloBot.
According to recent research by BitSight, the number of unique hosts has decreased from a peak of 250,000 in 2020 to “now witnessing more than 50,000 unique infected systems every day.”
Additionally, connections to BHProxies, a home proxy service, were discovered in the infrastructure of MyloBot, suggesting that the latter is using the compromised machines.
MyloBot first appeared in the threat environment in 2017, and Deep Instinct first identified it in 2018, highlighting its anti-analysis and downloader capabilities.
Black Lotus Laboratories at Lumen stated in November 2018, “What makes Mylobot hazardous is its capability to download and execute any form of payload when it infects a victim.” This implies that it could at any time download whatever further malware the attacker chooses.
The malware was seen sending extortion emails from compromised endpoints last year as part of a campaign with a financial goal of obtaining more than $2,700 in Bitcoin.
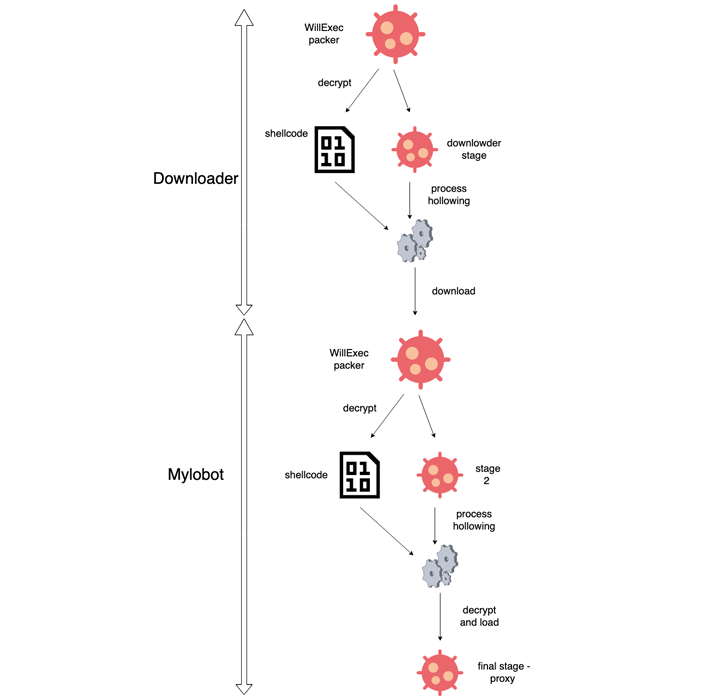
It is well known that MyloBot uses a multi-step process to unpack and run the bot virus. Significantly, it waits 14 days to avoid detection before attempting to reach the command-and-control (C2) server.
The primary purpose of the botnet is to connect to a hard-coded C2 domain encoded in the virus and wait for further instructions.
According to BitSight, “Mylobot turns the infected machine into a proxy when it receives a command from the C2.” The compromised device will be able to manage numerous connections and relay communications coming from the command-and-control server.
The malware has since evolved to use a downloader to connect to a C2 server, which then replies with an encrypted message containing a link to download the MyloBot payload.




