Longtime advocates of password restrictions that prevent users from using their old passwords again include IT security experts.
For instance, Netwrix advises configuring your password history policy to save at least the ten most recent passwords for each user. Microsoft also advises setting the password history to only save the last 24 passwords.
Unfortunately, end-user password reuse is a common practise that isn’t expected to stop anytime soon. In fact, 65% of end users openly acknowledge using the same password on one or more accounts—or even all of them.
How Password History Can Help
Microsoft, NIST, and other organisations now advise against mandating frequent password changes. It frequently lowers password security to force people to change their passwords merely because “it’s time.”
Users are more likely to use weak passwords, write down their passwords, or participate in other unsafe activity as a result of burnout or annoyance when they are obliged to change their passwords regularly.
On the other hand, if a company that follows these best practises for passwords requires customers to change their passwords, there is typically a valid reason for doing so. The password might have been compromised, or the security team of the company might think that a threat exists that calls for a password reset.
Password history becomes relevant in this situation.
A user could circumvent the requirements by changing their password and then instantly going back to their original password unless an organisation implements a password history requirement.
The user has fulfilled the password change criteria, according to the system. Naturally, this poses the same risk to the company as if the user had never changed their password in the first place.
By making it more challenging for a user to re-use their old password, password history restrictions deter this kind of conduct. Windows is forced by such a policy to keep track of recently used passwords in an effort to stop their re-use.
Implementing Password Change History
A password history requirement can be easily added to an existing password policy in Windows. Open the group policy object holding the current password policy to start the process.
Next, go to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy in the console tree of the Group Policy Management Editor.
Select the quantity of passwords you want Windows to remember by double clicking the Enforce Password History setting, as shown in Figure 1. To complete the procedure, click OK.
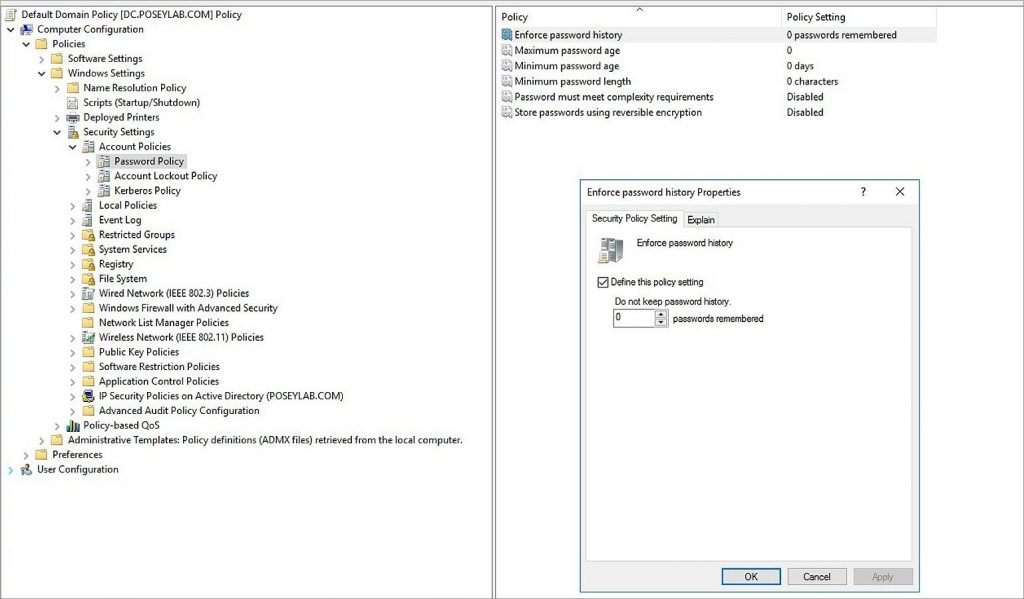
Figure 1 Password history requirements can be implemented at the group policy level.
Why Password Change History Alone Isn’t Enough
Windows can be set up to remember a user’s most recent passwords, which can help prevent that password from being used again anytime soon. However, there are ways for users to get around this policy.
Imagine, for example, if a user discovers that a company’s password policy is set up to save the six most recent passwords. Simply changing the password six times in a row would allow the user to return to the original password. Even though it’s likely that the majority of users won’t go to such measures to get around the password policy, there will definitely be some who do.
Enabling the Minimum Password Age setting, as you can see in the figure above, is one way to stop this kind of behaviour. A motivated user can swiftly cycle through a number of password changes until they reach the point where they are permitted to reuse their original password because Windows by default permits a recently changed password to be changed again right away.
Users are prevented from immediately changing their passwords again by enabling the Minimum Password Age setting. Assume, for instance, that you configured Windows to remember 24 passwords and that the minimum password age is set to one day.
That would imply that it would take 24 days for even the most dedicated user to be able to cycle back to their original password. The user will probably find it much simpler to simply accept their new password.
Users can also avoid password history requirements by using sequential passwords on occasion. The same root password may be used, but the user may add a number or the name of a month to the end of the password.
The user just increases the number or modifies the month of their password each time a change is necessary.
Unfortunately, this kind of password abuse cannot be stopped by Windows natively. Sequential passwords and other related tactics can be avoided by using Specops Password Policy. Additionally, administrators can identify phrases that are prohibited from being used in user passwords using Specops Password Policy. This enables you to prevent users from adding a month’s name to their password. It is always free to try out in your Active Directory.
Reference : bleepingcomputer.com/news/security/enforcing-password-history-in-your-windows-ad-to-curb-password-reuse/





