Within two months of its release into the wild, the Black Basta ransomware-as-a-company (RaaS) syndicate has amassed nearly 50 victims in the United States, Canada, the United Kingdom, Australia, and New Zealand, making it a significant threat in a shorter span.
Cybereason noted in a research that “Black Basta has been seen targeting a range of businesses, including manufacturing, construction, transportation, telecommunications, prescription pharmaceuticals, cosmetics, plumbing and heating, vehicle dealers, underwear companies, and additional.”
Black Basta is thought to use double extortion, a tried-and-true method of ransomware operation, to steal sensitive information from its targets and threaten to disseminate the stolen information unless a digital payment is made.
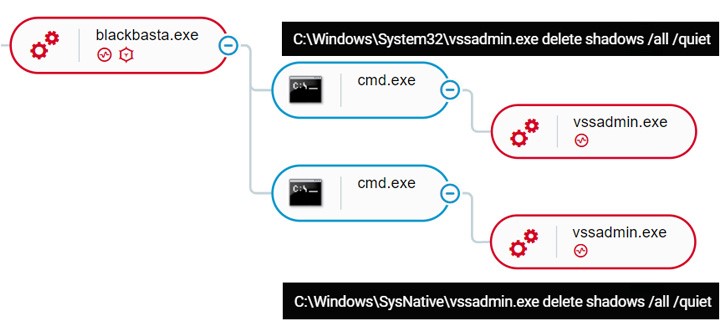
Intrusions using the risk, a newcomer in the previously popular ransomware environment, have used QBot (also known as Qakbot) as a conduit to maintain persistence on the compromised servers and gather credentials before spreading laterally across the network and deploying the file-encrypting malware.
Additionally, the people behind Black Basta have created a Linux variant designed to attack VMware ESXi virtual machines (VMs) operating on enterprise servers, putting them on level with other organisations like LockBit, Hive, and Cheerscrypt.
According to security expert Ido Cohen, the cybercriminal organisation added Elbit Techniques of the United States, a producer of defence, aerospace, and security options, to its list of victims over the weekend.
According to reports, Black Basta is made up of users from the Conti group, which shut down its operations in response to increased law enforcement scrutiny and a significant leak in which its tools and methods were seen in the community after siding with Russia in that nation’s conflict with Ukraine.
According to the Ukrainian computer expert who leaked the information under the alias Danylo and described it as a form of digital vengeance, “I are unable to shoot practically anything, but I can fight with a keyboard and mouse,” he told CNN in March 2022.
Since then, the Conti team has denied any connection to Black Basta. Last Monday, it formally ended the illegal organisation by decommissioning the last of its public-facing infrastructure, including two Tor servers used to leak information and bargain with victims.
While some team members moved on to other ransomware organisations and the brand underwent an organisational overhaul that saw it fragment into smaller subgroups with different motivations and business offerings ranging from information theft to working as independent affiliate marketers, the team continued to maintain the appearance of an active procedure by focusing on the Costa Rican government administration.
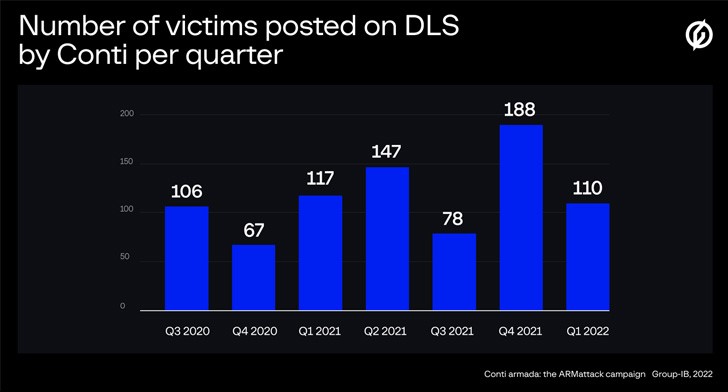
The Conti team is believed to have compromised over 40 businesses worldwide as part of a “lightning-quickly” hacking spree that lasted from November 17 to December 20, 2021, according to a detailed report from Group-IB outlining its activities. This is considering that it was initially noticed in February 2020.
The incursions, code-named “ARMattack” by the Singapore-based company, were mostly intended against American enterprises (37%) and were also used by Germany (3%) and the United Arab Emirates (2%) as well as the Netherlands, Spain, France, the Czech Republic, Sweden, Denmark, and India (1 percent every).
Ivan Pisarev of Group-IB stated that “Conti’s enhanced activity and the data leak suggest that ransomware is no longer an activity among typical malware builders but rather an illicit RaaS marketplace that presents work to hundreds of cybercriminals throughout the world with a variety of specialisations.”
Conti is a notorious player in this industry who, as an example, founded a ‘IT firm’ with the purpose of extorting large quantities of money. It is clear that the group will carry out its duties, either independently or with the aid of its “subsidiary” enterprises.
Reference: https://rushhourtimes.com/cybersecurity-experts-warn-of-emerging-threat-of-black-basta-ransomware/



