Threat actors harvest user credentials by exploiting Instagram’s highly sought-after verification programme.
Vade discovered a sophisticated and targeted phishing campaign aimed at luring Instagram users into a trap and stealing their personal information and account credentials.
It starts by email informing you that your Instagram account has been reviewed and determined to be eligible for verification. Grammatical errors and typos, as is common in phishing emails, reveal the threat actors. The email also urges immediate action, which is another telltale sign of a scammer. Of course, malicious hackers hope that victims will ignore the telltale signs of a scam and click on the “Badge Form”. Victims are redirected to a malicious website after clicking on the link.
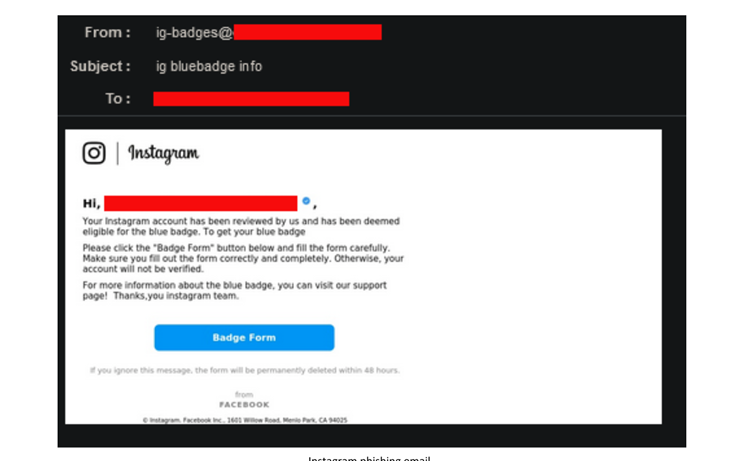
“Here, hackers hope that the victim believes Instagram uses a website other than instagram.com to verify users”. They attempt to create the illusion of authenticity once more by displaying Instagram’s brand colors and the logo of its parent company, Meta. They also make a number of grammatical errors,” Vade explained.
The website prompts users to enter the following information for verification: the victim’s Instagram handle, name, email, phone number, and, eventually, password. After entering information, the website displays a seemingly innocuous message that says, “Thank you for verifying your account. Our staff will get back to you as soon as possible. (Avg. 48 hours.).
Vade predicted that the Instagram phishing campaign began on July 22, 2022, with emails 1,000 per day on two occasions.
“At this time, the malicious campaign appears to be small in scale,” Vade said. It would support the targeted nature of the attacks.




