Iranian state-sponsored actors are doing all in their power to target Israeli entities using unpatched Log4j systems; this shows how long the vulnerability will take to fix.
The most recent operations were attributed by Microsoft to the umbrella threat group known as MuddyWater. Also known as Cobalt Ulster, Mercury, Seedworm, or Static Kitten), which is connected to the Iranian intelligence apparatus and the Ministry of Intelligence and Security (MOIS).
The assaults stand out because they use SysAid Server machines that are vulnerable to the Log4Shell issue as a vector for first access, departing from the actors’ prior practice of using VMware programmes to enter target environments.
After gaining control, Mercury creates persistence, dumps credentials, and advances laterally inside the targeted company using both custom and well-known hacking tools. As well as specially created operating system programmes for its hands-on keyboard attack, according to Microsoft.
The attacks were witnessed, according to the threat intelligence division of the IT giant, on July 23, 2022.
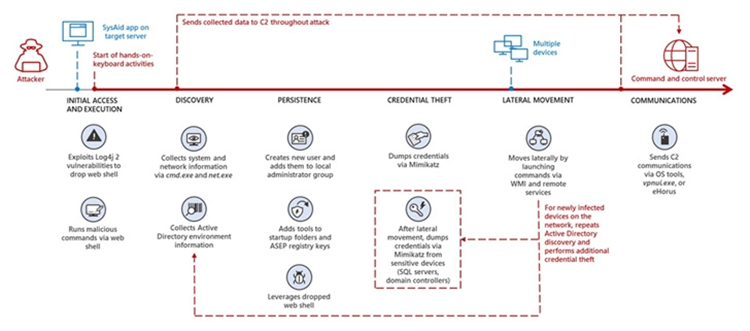
The deployment of web shells to execute instructions that enable the actor to conduct reconnaissance, generate persistence, steal qualifications, and promote lateral motion is reportedly what came after a successful compromise.
A remote monitoring and administration computer programme is known as eHorus and Ligolo. A reverse-tunneling tool of choice for the adversary is also used for command-and-management (C2) contact during invasions.
The findings come as the Cyber Security Review Board (CSRB) of the U.S. Department of Homeland Security (DHS) deemed the significant vulnerability in the open-source Java-based logging framework as an endemic flaw that will continue to afflict businesses for decades to come as exploitation evolves.
Many vendors’ software and services use Log4j widely, it is likely that cunning adversaries like state-sponsored actors and market participants have opportunistically exploited the vulnerability to launch a variety of assaults.
The Log4Shell attacks also coincide with a recent Mandiant investigation that identified an espionage effort by a suspected Iranian hacker cell known as UNC3890. They targeted Israeli transportation, the federal government, energy, and healthcare institutions.





