Threat actors are increasingly imitating trustworthy programmes like Skype, Adobe Reader, and VLC Player in order to take advantage of trust connections and raise the chance that a social engineering attack would be successful.
According to a VirusTotal investigation, other commonly imitated genuine apps by icon include 7-Zip, TeamViewer, CCleaner, Microsoft Edge, Steam, Zoom, and WhatsApp.
Making a malware sample appear to be a legitimate programme is one of the easiest social engineering methods we’ve seen, according to a report released by VirusTotal on Tuesday. “A crucial element utilized to persuade victims that these services are authentic is the symbol of these applications.”
It comes as no surprise that threat actors deploy a number of strategies to infiltrate endpoints by coercing unaware users into downloading and executing ostensibly harmless executables.
This is then mostly accomplished by using legitimate domains to circumvent IP-based firewall protections. Top abused domains include qq.com, amazonaws.com, mediafire.com, squarespace.com, and discordapp.com.
There have been found to have been 2.5 million malicious files downloaded from 101 of the top 1,000 websites according to Alexa.
The abuse of Discord has been well-documented, with the platform’s content delivery network (CDN) serving as an “ideal communications center for attackers” and serving as a “fertile ground for storing malware alongside Telegram.”
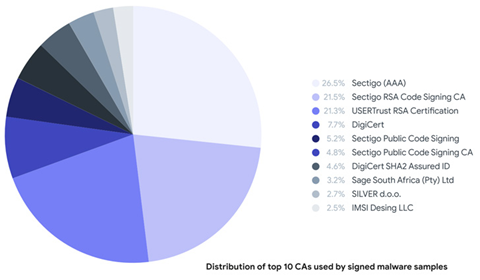
Malware signing with legitimate certificates obtained by stealing them from other software developers is another often utilized tactic. Since January 2021, the malware scanning service claims to have discovered over one million dangerous samples, 87 percent of which already had a valid signature when they were first uploaded to its database.
Since January 2020, VirusTotal claims to have found 1,816 samples of malware that was disguised as genuine software by being packaged in installers for other well-known programs like Google Chrome, Malwarebytes, Zoom, Brave, Mozilla Firefox, and Proton VPN.
When hackers are successful in breaking into a legitimate software’s update server or obtaining illegal access to the source code, they may be able to smuggle malware in the form of trojanized binaries, creating a supply chain.
Instead, genuine installers are being bundled with malicious files in compressed files, in one instance including the Jigsaw ransomware installation and the Proton VPN installer.
Not only that. A third, more advanced technique involves including the genuine installer as a portable executable resource in the malicious sample. This way, when the malware is run, the installer is also executed, giving the impression that the software is functioning as intended.
“When thinking about these techniques as a whole, one could conclude that there are both routinely (most likely) automated procedures where attackers aim to visually replicate applications in different ways, as well as opportunistic factors for the attackers to abuse (like stolen certificates) in the short and mid-term,” the researchers said.





