Security experts have revealed previously unknown spyware that targets the Apple macOS operating system.
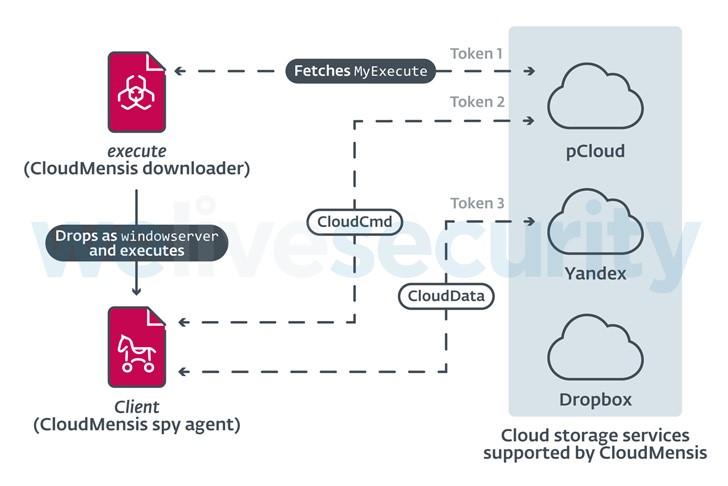
The malware, known as CloudMensis by the Slovak cybersecurity company ESET, is rumoured to only use open-source cloud storage platforms like pCloud, Yandex Disk, and Dropbox to receive commands from attackers and exfiltrate files.
In a paper released today, ESET researcher Marc-Etienne M.Léveillé stated that the malware’s capabilities “clearly reveal that its operators’ purpose is to gather information from the victims’ Macs by exfiltrating documents, keystrokes, and screen captures.”
The Objective-C malware known as CloudMensis was first identified in April 2022 and is intended to attack both Apple and Intel chip designs. Targets and the primary infection vector for the attacks are still unknown. However, the malware’s extremely restricted use suggests that it is being employed in a highly focused attack on important targets.
The attack chain discovered by ESET makes advantage of administrator rights and code execution to launch a first-stage payload that is then used to fetch and run a second-stage virus housed on pCloud, which in turn exfiltrates data like screenshots, email attachments, and documents.
The fact that the first-stage downloader is known to remove evidence of Safari sandbox escape and privilege escalation exploits that employ four security flaws that have been fixed in 2017 suggests that CloudMensis may have remained unnoticed for a long time.
The implant also has tools to go beyond the Transparency, Consent, and Control (TCC) security system, which requires all apps to get permission from users before accessing files in Documents, Downloads, Desktop, iCloud Drive, and network volumes.
It accomplishes this by taking advantage of a different patched security flaw identified as CVE-2020-9934 that was discovered in 2020. The backdoor also has the ability to perform shell commands and other arbitrary payloads, list files on removable storage devices, list processes that are currently operating, take screenshots, and list files.
The pCloud accounts were formed on January 19, 2022, and a review of the metadata from the cloud storage infrastructure reveals that compromises started on February 4 and peaked in March.
According to M.Léveillé, “the general quality of the code and lack of obfuscation shows the authors may not be particularly experienced with Mac development and are not that sophisticated.” “However, considerable effort was made to make CloudMensis an effective surveillance tool and a threat to possible targets.”
Reference : thehackernews.com/2022/07/experts-uncover-new-cloudmensis-spyware.html