A critical security vulnerability in the Amazon ECR (Elastic Container Registry) Public Exhibition could have enabled assailants to deactivate any container image or inject malware into images from other AWS accounts.
The Amazon ECR Public Gallery is a general populace repository of image data used to share ready-to-use applications. And famous Linux distributions such as Nginx, EKS Distro, Amazon Linux, CloudWatch agent, and Datadog agent. The flaws in Amazon ECR Public Gallery.
A Lightspin security specialist discovered a new flaw in the ECR Open Gallery that allows users to alter other users’ actual public images, layers, tags, registries, and repositories by abusing unregistered API actions.
Also, read Several Amazon RDS instances are disclosing user data.
On November 15, 2022, the researcher stated the security vulnerabilities of AWS Security. Amazon fixed it in less than 24 hours.
While there are no signs of this flaw being abused in the wild. Threat actors could have used it in massive-scale supply chain attacks against many users.
Characteristically, the top six most downloaded container images in ECR Public Gallery have had over 13 billion downloads, so any malicious injection in them could have resulted in “out-of-control” infections.
Lightspin says its analysis showed that 26% of all Kubernetes clusters have at least one pod that pulls an image from ECR Public Gallery so the repercussions could have been significant.
Leveraging undocumented ECR API actions
Lightspin’s study observed that ECR Public Gallery had many internal API actions employed to support custom functions and user actions. But none of them were publicly exposed.
Four API actions mentioned below lacked triggers but remained active on the console and thus could be invoked.
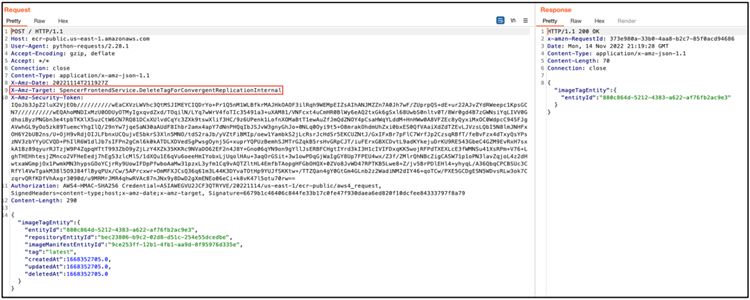
DeleteImageForConvergentReplicationInternal
DeleteTagForConvergentReplicationInternal
PutImageForConvergentReplicationInternal
PutLayerForConvergentReplicationInternal
The analyst forged malicious API requests that would be accepted after figuring out how to verify against the ECR internal API using momentary login details from Amazon Cognito.
Of course, for the preceding to work, the request must have a valid JSON structure, which required some experimentation due to the lack of documentation for these API calls.
The request in Lightspin’s proof of concept example uses the “DeleteImage” API call. It is available to the public repository and picture IDs to wipe an available public image posted by the researcher.
The exploit steps were baked into a Python code, so the process may have been automated to exploit the undocumented API calls to strike public personas.
Amazon’s Response
Amazon said that the issue discovered by Lightspin was immediately resolved. Amazon started an internal investigation that revealed no evidence of oppression by malicious actors.
The internet giant is proficient because no consumer account holders, uploads, or other resources have been compromised based on the logs and evidence examined.
The following is Amazon’s full statement:
On November 14, 2022, a security researcher discovered a bug in Amazon Elastic Container Registry (ECR) Public Gallery. It is a public website for finding and sharing public container images. The vulnerability is an ECR API action, if invoked, could have allowed for the alteration or withdrawal of images from the ECR Public Gallery.
The identified issue had been resolved as of November 15, 2022. We conducted a thorough examination of all logs. Amazon confidently said the investigation is complete and the sole activity associated is with accounts owned by the analyst. There was no impact on other customers’ accounts, and no client action was required. We want to applaud Lightspin for alerting us to this problem.





