Based on the evidence of active exploitation, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added two new vulnerabilities to its list of known exploited vulnerabilities.
One of these has been a zero-day defect in the Windows Support Diagnostic Tool (MSDT) for more than two years, and the exploit code for it is readily available online.
Both security flaws are directory traversal vulnerabilities with a high severity rating that could allow attackers to infect a target system with malware.
Windows DogWalk bug
The security hole in MSDT, officially tracked as CVE-2022-34713 and colloquially known as DogWalk, enables an attacker to insert a malicious programme into the Windows Startup folder.
Imre Rad, a researcher, first alerted Microsoft to the problem in January 2020, but his report was incorrectly labeled as not detailing a security risk and disregarded as such.
Security researcher j00sean brought the issue back to the public’s notice this year by summarising what an attacker could do by exploiting it and providing video evidence:
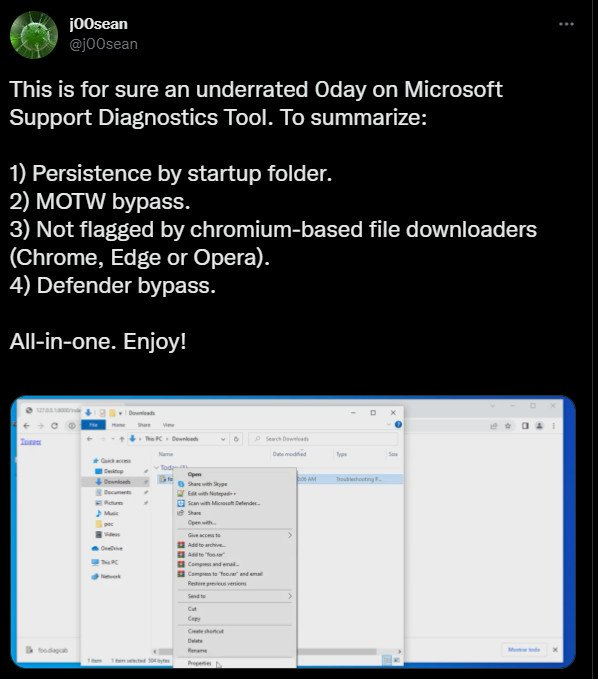
In a warning released today, Microsoft notes that successful exploitation necessitates user involvement, a challenge easily overcome through social engineering, particularly in email- and web-based attacks:
An attacker could take advantage of the flaw in an email attack by emailing the victim a specially designed file and persuading them to open it.
In a web-based attack scenario, an attacker may run a website (or make use of a website that has been compromised that accepts or hosts user-provided content) that contains a specially created file intended to exploit the vulnerability.
Since early June, an unauthorized patch for the majority of the impacted Windows versions (Windows 7/10/11 and Server 2008 through 2022) has been available from the 0patch micropatching service.
In the Windows security updates for August 2022, Microsoft fixed CVE-2022-34713. The business acknowledges that assaults have made use of the problem.
UnRAR bug exploited
The second vulnerability, tagged as CVE-2022-30333, is a path traversal flaw in the Linux and Unix system software UnRAR. It was uploaded to CISA’s Known Exploited Vulnerabilities Catalog.
By extracting it to any location at will during the unpacking process, an attacker may use it to install a malicious file on the target system.
A study detailing how it may be exploited for remote code execution to breach a Zimbra email server without authentication was released by the Swiss company SonarSource in late June. The penetration testing tool Metasploit recently received an addition of exploit code.
Federal agencies in the United States are required to implement vendor patches for both vulnerabilities by August 30.





