With the promise of stealing authentication tokens to get around multi-factor authentication (MFA) on Apple, Google, Facebook, Microsoft, Twitter, GitHub, GoDaddy, and even PyPI. A reverse-proxy phishing-as-a-service (PaaS) platform named EvilProxy has surfaced.
The service made possible for low-skill threat actors to steal internet accounts that are otherwise well-protected. This is because they don’t know how to set up reverse proxies.
Reverse proxies are servers that stand in the way of a targeted victim and a trusted authentication endpoint, like a business login page. When the victim connects to a phishing page, the reverse proxy displays the legitimate login form, forwards requests, and returns responses from the company’s website.
The victim is forwarded to the actual platform’s server after providing their credentials and MFA on the phishing page, where they are logged in and receive a session cookie. The proxy used by the threat actor can also steal the session cookie containing the authentication token because it is in the middle of the process. Bypassing the set up of multi-factor authentication security measures, the threat actors can then log into the website using authentication cookie as the user.
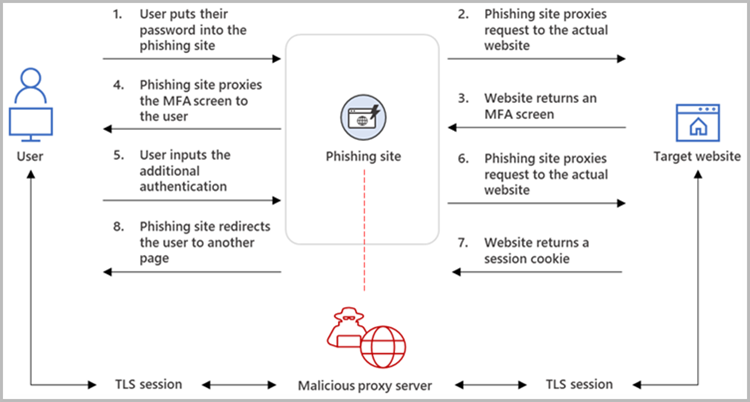
Sophisticated APT groups use reverse proxies to get around MFA safeguards on target accounts for some time now. Some of these groups use their own bespoke tools, while others use easier-to-use kits like Modlishka, Necrobrowser, and Evilginx2.
When comparing phishing frameworks with EvilProxy, they are easier to set up, provides in-depth training and instructional videos. Phising framework has intuitive graphical user interface, and offers a wide variety of cloned phishing pages for well-known online businesses.
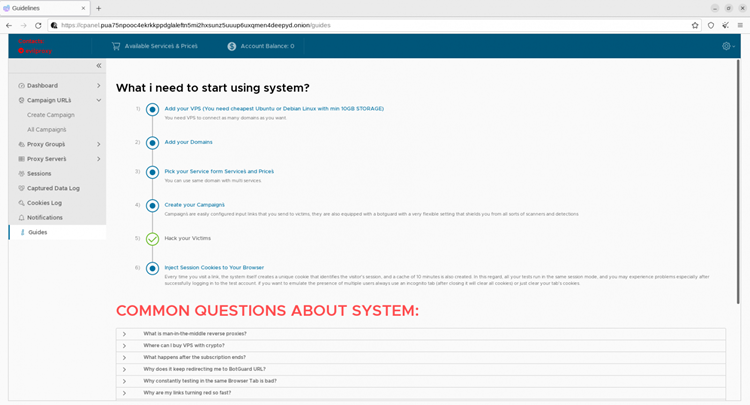
A deeper look at EvilProxy
EvilProxy, according to Resecurity, provides a simple-to-use GUI where threat actors can set up and manage phishing campaigns and information goes with them.
The service asks for $150 for ten days, $250 for twenty days, or $400 for a month-long campaign. The service in exchange for the promise to obtain usernames, passwords, and session cookies. Attacks against Google accounts are more expensive, costing $250/450/600.
The next video from Resecurity shows how an assault on a Google account would go using EvilProxy.
Although the service frequently advertised on numerous clearnet and dark web hacking communities. Some potential customers are probably turned down since the operators vet the clients.
Resecurity claims that each customer arranges their own payment for the service via Telegram. The customer accesses the portal housed on the onion network after paying the deposit (TOR).
According to Resecurity’s evaluation, EvilProxy also provides VM, anti-analysis, and anti-bot protection to weed out erroneous or unwanted visits to the phishing sites it hosts.
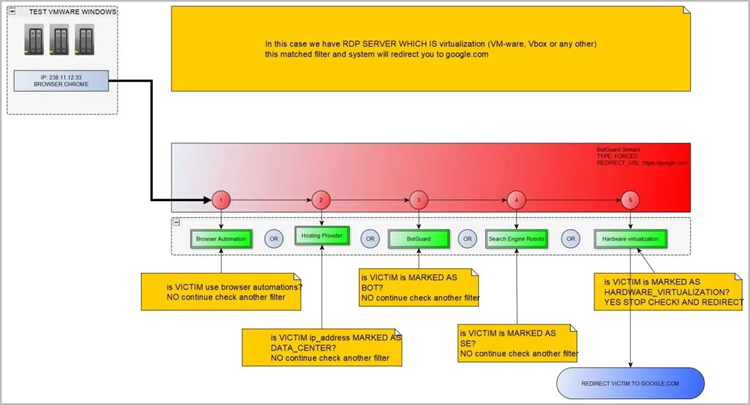
Resecurity stated “the bad actors use a variety of strategies and approaches to distinguish victims and to keep the phishing-kit code from identification”.
They gather information about well-known VPN services, Proxies, TOR exit nodes, and other hosts that may be utilized for IP reputation analysis (of potential victims), much like fraud prevention and cyber threat intelligence (CTI) solutions.
A service to look out for
Reverse-proxy tools are becoming more popular among threat actors as MFA acceptance rises. The advent of a platform that streamlines everything for criminals is bad news for security experts and network administrators.
For time being, the only solution is to use client-side TLS fingerprinting to detect and block requests from MitM attacks. The industry’s status of its implementation, meanwhile, is out of step with the changes.
Thus, tools like EvilProxy effectively bridge the gap and give low-level threat actors a cheap approach to taking valuable accounts.




