Researchers have given the backdoor IceBreaker the name because it appears to be used by hackers to attack internet play and gambling businesses.
The compromising technique depends on convincing customer care representatives to open infected screenshots that a threat actor sends pretending to be a user with a problem.
Since September 2022, these assaults have been taking place. There are vague hints that lead to the origin of the group behind them, but they are yet unidentified.
The IceBreaker backdoor, according to experts at incident response company Security Joes, is the work of a new sophisticated threat actor who employs “a very specialized social engineering approach,” which may help identify them.
Security Joes reacted to three further attacks before the attackers could breach their targets. Thanks to data analysis from a September event.
Also, read YouTube gaming videos help distribute new malware packs.
The researchers claim that a tweet by MalwareHunterTeam in October was the only publicly available proof they could locate of an IceBreaker threat actor.
Tricking customer service
The threat actor contacts the target company’s customer support claiming to be a user having trouble checking in or enrolling for the online platform to deploy the backdoor.
The hackers get the customer service representative to obtain an image more accurately illustrates the issue than they can. Although they also observed it being supplied from a Dropbox storage. The researchers claim that the image is often stored on a fake website that pretends to be a reputable provider.
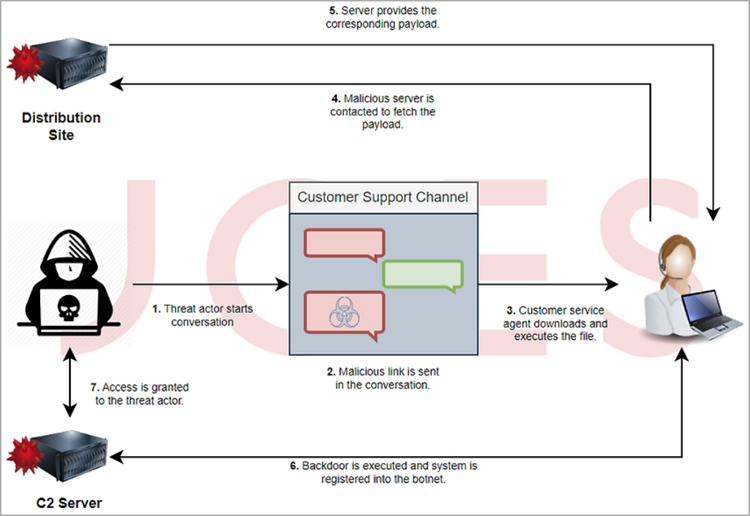
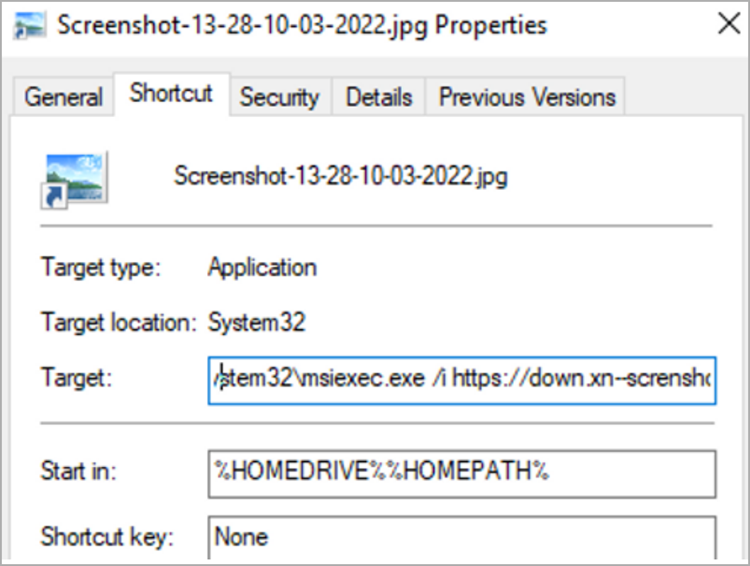
The links sent in this manner open a ZIP archive of maliciously crafted LNK files that download the IceBreaker backdoor or the Houdini RAT, which has been operational since at least 2013. The logo for the Windows Shortcuts file has been altered to make it appear innocent, as shown below. A command to download an MSI payload from the assailant’s server and install it without user input. And run it without a user interface contained in the shortcut.
According to Security Joes researchers, the malware downloaded is “a massively complicated compiled JavaScript file” that can find out what processes are running and steal data, biscuits, and files. Open a proxy corridor for the attacker, and execute scripts downloaded from the attacker’s server.
The IceBreaker backdoor
To deploy the IceBreaker virus, the malicious LNK serves as the primary first-stage payload. The VBS file is a backup if the customer care agent cannot launch the shortcut.
The rogue shortcut file has its extension changed to match the JPG image it pretends to be. Only 4 out of 60 scans for the MSI payloads it downloads on Virus Total end up as positive results.
Also, read Hackers use a fraudulent Pokemon NFT game to hack Windows devices.
The MSI package includes many bogus files to get beyond signature-based detection methods and analysis engines. The “Port.exe” payload is dropped onto the victim’s temporary folder via a CAB archive extracted as the final layer.
According to Security Joes, this is a C++ 64-bit executable with an odd overlay that keeps some of the data added to the file’s end. According to the analysts, this is a technique for hiding extra resources from security software.
After additional examination, Security Joes discovered that the sample is a Node.js module backdoor that gives threat actors access to the following features:
- Extension of the malware’s built-in features through customization via plugins.
- Process exploration.
- Steal cookies and passwords from local storage, especially Google Chrome.
- A Socks5 reverse proxy server should be enabled.
- Create a new LNK file (WINN.lnk) in the Windows starting folder to establish persistence.
- Utilize web sockets to leak files to the remote server.
- Execute unique VBS scripts.
- Snapshots are taken.
- Create shell sessions over a distance.
The threat actors can utilize the backdoor to steal login details and travel laterally in the network. Further, their infiltration if the targeted company has not contracted out customer support services to an outside supplier.
Recommendation
Since little is currently known about the IceBreaker group, Security Joes decided to publish a report on their discoveries and reveal all IoCs (indicators of compromise) they have discovered to assist defenders in identifying and countering this threat.
The researchers released a technical study detailing the threat actor’s methods and backdoor’s operation. Additionally, YARA regulations have been released to aid enterprises in malware detection.
Additionally, Security Joes advises businesses concerned about an IceBreaker breach to search the startup folder for shortcut files and look out for unauthorized usage of the open-source programme tsocks.exe. As with running VBS scripts and LNK files from the temporary file, keeping an eye on the development of msiexec.exe processes that take URLs as parameters could be a sign of compromise.





