Small office/home office (SOHO) routers have been singled out by a previously unknown remote access trojan known as ZuoRAT as part of a sophisticated operation aimed at North American and European networks.
According to experts at Lumen Black Lotus Labs, the malware “gives the actor the opportunity to pivot into the local network and get access to more devices on the LAN by hijacking network communications to retain an undetected presence.”
The covert operation, which targeted routers made by ASUS, Cisco, DrayTek, and NETGEAR, is said to have started in the early months of the COVID-19 outbreak in 2020. As a result, it went unnoticed for more than two years.
The company’s threat intelligence team stated that SOHO routers are frequently used by consumers and remote workers, but that they are rarely checked or patched, making them one of the weakest spots of a network’s perimeter.
The remote access tool is used to gain network access and drop a next-stage shellcode loader that is used to deliver Cobalt Strike and custom backdoors such as CBeacon and GoBeacon that are capable of executing arbitrary commands. The initial access to the routers is obtained by scanning for known unpatched flaws.
The malware has been described as a substantially modified variant of the Mirai botnet, whose source was leaked in October 2016, and is capable of comprehensive reconnaissance of target networks, traffic collecting, and network communication hijacking.
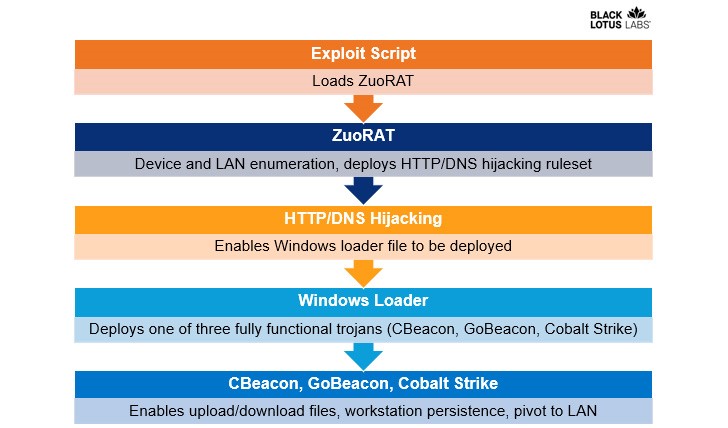
The researchers explained that ZuoRAT is a MIPS file built for SOHO routers that can enumerate hosts and internal LANs, intercept packets travelling via the infected device, and carry out person-in-the-middle attacks (DNS and HTTPS hijacking based on established rules).
The adversary may be able to monitor user internet behavior by using a function to harvest TCP connections through the FTP and web browsing ports of 21 and 8443, respectively, which are also included in the compromised router.
With the help of ZuoRAT’s additional features, attackers are able to keep an eye on DNS and HTTPS traffic with the intention of hijacking requests and rerouting victims to malicious domains using pre-made rules that are generated and stored in temporary directories in an effort to evade forensic analysis.
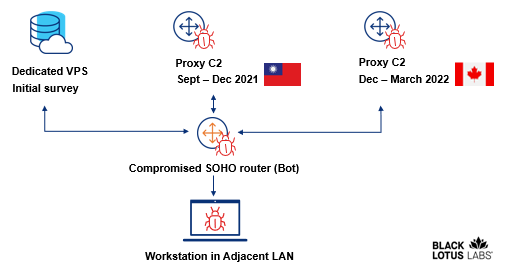
The hackers also used a virtual private server to drop the original RAT vulnerability and infected routers as proxy C2 servers, so these are not the only steps they used to hide their activity. The attacks rely on a complex, multi-stage C2 architecture.
The staging server has been seen displaying seemingly innocent information to further evade discovery, including one occasion when it imitated the website “muhsinlar.net,” a propaganda platform created for the Turkestan Islamic Party (TIP), an Islamist Uyghur group with Chinese roots.
Although an investigation of the artefacts showed potential allusions to the Chinese region of Xiancheng and the employment of Alibaba’s Yuque and Tencent for command-and-control, the name of the antagonistic collective behind the effort is still unknown (C2).
According to Black Lotus Labs, the operation’s intricate and evasive design and the strategies used in the attacks to maintain cover all points to possible nation-state action.
The abilities shown in this campaign—gaining access to SOHO devices of various makes and models, gathering host and LAN data to inform targeting, sampling and hijacking network communications to potentially gain persistent access to in-land devices, and intentionally stealth C2 infrastructure utilizing multistage siloed router to router communications—point to a highly sophisticated actor, the researchers said.
Reference: https://blog.lumen.com/zuorat-hijacks-soho-routers-to-silently-stalk-networks/





