The Microsoft Threat Intelligence Center (MSTIC) and Microsoft 365 Defender Research Team have recently discovered Iran-based threat actor MERCURY using SysAid applications’ exploits of Log4j 2 vulnerabilities to target enterprises that are all in Israel. The Ministry of Intelligence and Security of Iran was connected to the activities that Mercury saw, according to MSTIC’s assessment with high confidence (MOIS).
MERCURY TTPs align with Iran-based nation-state actor
Microsoft estimates that MERCURY exploited weak SysAid Server instances the targets were running in order to take advantage of remote code execution flaws in Apache Log4j 2 (commonly known as “Log4Shell”). Additionally, MERCURY has utilized Log4j 2 exploits in prior operations.
The Ministry of Intelligence and Security of Iran, according to MSTIC, is cooperating with Mercury to coordinate its actions (MOIS). MuddyWater, a group we track as MERCURY, “is a subordinate unit within the Iranian Ministry of Intelligence and Security,” according to the US Cyber Command.
Observed actor activity
MERCURY was seen exploiting vulnerabilities against weak SysAid Server instances as its initial access vector on July 23, 2022. Microsoft determines that the exploits employed were probably connected to Log4j 2 based on observations from prior campaigns and vulnerabilities discovered in target environments. In 2022, the threat actor used Log4j 2 attacks against VMware applications and probably looked for other internet-facing apps. Given its position in the targeted nation, SysAid may have appeared to be an alluring target.
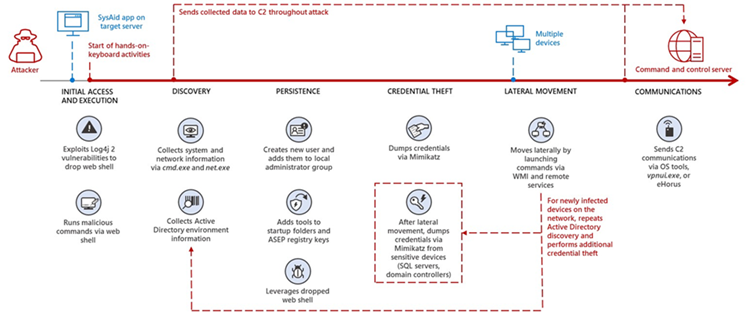
The threat actor can drop and use web shells to run the instructions listed below by successfully exploiting SysAid. With the exception of one PowerShell action that downloads the actor’s tool for lateral movement and persistence, most commands are linked to reconnaissance.
Recommended customer actions
Implement the following security recommendations to minimize the approaches employed by the actor and outlined in the previous section:
- Verify whether SysAid is installed on your network, if yes, update any impacted products and services soon and deploy fixes. For technical details about the vulnerabilities and mitigation advice, see SysAid’s Important Update Regarding Apache Log4j.
- For information on preventing, detecting, and searching for the Log4j 2 vulnerabilities, see the complete guidance.
- Investigate their existence in your environment and assess any potential intrusions using the indicators of compromise that are presented.
- Block incoming traffic from the IP addresses included in the table of indicators of compromise.
- To ensure validity, look at unusual activity, review all authentication activity for the remote access infrastructure, paying special attention to accounts set up using single-factor authentication.
- Enable multi-factor authentication (MFA) and ensure to enforce remote connectivity to reduce the risk of credentials being compromised. Note: To secure accounts, Microsoft highly advises all customers to download and use password-less solutions like Microsoft Authenticator.