A recent research report by Menlo Security revealed that the threat actors had delivered PureCrypter malware downloader through Discord to target government entities.
Discord is a community chat app used by millions of people. The threat actor used Discord to host the payload and compromised a non-profit organization for storing the extra hosts in the campaign.
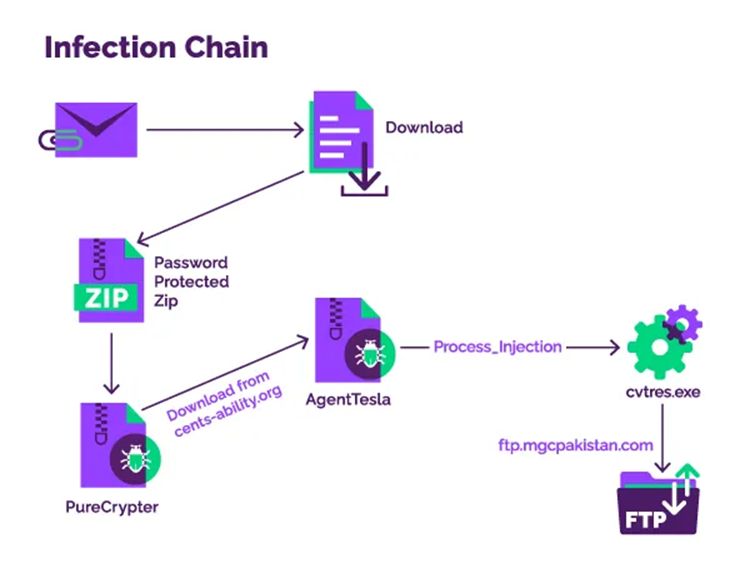
The PureCrypter malware also delivered secondary payloads such as Eternity, Redline stealer, Philadelphia, and Agent Tesla ransomware. The initial investigation of Menlo Security started when their security platform blocked the password-protected archive files of many government customers.
Attack Vector
PureCypter was first seen in March 2021 and is a malware downloader .NET-based. Its owner leases it out to other online offenders so they can disseminate different kinds of malware.
When it is executed, the compromised server of a non-profit group serves as the next-stage payload from a compromised command and control server.
AgentTesla was the sample that the Menlo Security experts examined. When it is started, it creates a connection to an FTP server in Pakistan, where the stolen data is then received.
The researchers discovered that to minimize their footprint and the risk of being identified, the threat actors used leaked credentials rather than setting up their FTP server to seize control of the specific server.
Additionally, it was discovered that AgentTesla was interacting with a Pakistani FTP server and used a process hollowing method to inject its payload into the common Windows process known as “cvtres.exe,” which is present in all Windows OS versions. The entire stolen data is also uploaded to the FTP site by AgentTesla.
The Rise of Agent Tesla
Hackers have been using the AgentTesla family of .NET malware for the past eight years. In late 2020 and early 2021, usage will be at its zenith.
According to a recent Cofense report, AgentTesla has been continuously developed and improved over the years and is still a highly effective and capable gateway.
Approximately one-third of all keylogger complaints Cofense Intelligence received in 2022 resulted from AgentTesla’s keylogging activity.
The malware can intercept data copied to the clipboard, such as texts, passwords, and credit card information. And then steal credentials stored in internet browsers, email accounts, or FTP clients. It can also take screenshots of the desktop that could disclose sensitive information.
Menlo Labs investigated several attacks, and it was found that the malicious actors used process eking to insert the AgentTesla payload into a legal process (cvtres.exe) to avoid being detected by antivirus software.
AgentTesla employs XOR encryption to shield its configuration files and interactions with the C2 server from network traffic analysis software.
Although Menlo Security considers the malicious actors behind the PureCrypter campaign minor. It is still essential to monitor their behavior because they are targeting government entities.
Before being forced to locate new infrastructure, the attacker will probably continue to use compromised facilities for as long as possible.



