A total of 542 domains, among them, permit any IP address to send emails on their behalf.
Sebastian Salla conducted an experiment around six months ago in which he attempted to identify Australian domains that were susceptible to IP takeover assaults using dangling SPF IP addresses. This project was a big success, and he discovered that 264 Australian organisations were exposed to this kind of assault.
At the conclusion of that test, he was left wondering: What other problems might be discovered through at-scale scanning of Australian SPF & DMARC records? and ultimately decided to put this research on hold, but this week he made the decision to resume it!
Describe SPF. The Senders Policy Framework (SPF) is a public record that businesses post on their Domain Name Server (DNS), and it often contains a list of IP addresses that inform recipient organisations of the IP addresses from which they may expect to receive genuine and allowed emails.
DMARC: What is it? An email authentication technique that works in conjunction with SPF and DKIM is called Domain-based Message Authentication, Reporting and Conformance (DMARC). Importantly for the purposes of this study, a fortified DMARC record also reduces the impact of the spf-bypass email spoofing attack.
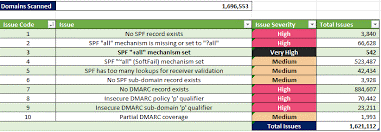
| # | Issue Title | Issue Detail | Severity |
| 1 | No SPF record exists | There is no SPF DNS record. Mail receivers have no mechanism to determine what the authorized mail servers are. Mail receivers will pass authentication checks with a “None” result, indicating no check could be performed. Spoofed emails are likely to be accepted. | High |
| 2 | No SPF “all” mechanism set or set to “?all” | The “all” mechanism at the end of the end of an SPF record tells receivers how to treat unauthorized (i.e., spoofed) emails – if the mechanism is missing or set to “?all”, failed authentication checks will always return a “Neutral” result which many receivers interpret to accept all mail from a domain (including spoofed emails). | High |
| 3 | SPF “+all” (Pass) mechanism set | The “all” mechanism at the end of an SPF record tells receivers how to treat unauthorized (i.e., spoofed) emails – the “+all” setting tells receivers to pass/accept all mail from a domain (including spoofed emails). | Very High |
| 4 | SPF “~all” (SoftFail) mechanism set | The “all” mechanism at the end of an SPF record tells receivers how to treat unauthorized (i.e., spoofed) emails – the “~all” setting tells receivers to ‘SoftFail’ (i.e., quarantine)) emails that fail SPF authentication. In practice, however, many email filters only slightly raise the total spam score and accept ‘oftFailed’ (i.e., spoofed) emails. | Medium |
| 5 | SPF has too many lookups for receiver validation | The SPF record requires more than 10 DNS lookups for the validation process. The SPF RFC states that a maximum of 10 lookups are allowed. As a result, recipients may throw a PermError instead of proceeding with SPF validation. Recipients treat these errors differently than a hard or soft SPF fail, but some will continue processing the mail (i.e., accept spoofed emails). | Medium |
| 6 | No SPF sub-domain record exists | The SPF sub-domain policy is a catch-all mechanism used to prevent threat actors from maliciously spoofing sub-domains from which an explicit SPF record hasn’t been set. This is typically represented through a DNS entry similar to “* IN TXT v=spf1 -all”, effectively telling recipients to block mail if an explicit SPF entry for the sub-domain hasn’t been set. | Medium |
| 7 | No DMARC record exists | There is no DMARC DNS Record set for the domain. Spoofed emails utilizing an attack technique known as SPF-bypass are likely to be accepted. See FAQs for more information. | High |
| 8 | Insecure DMARC policy ‘p’ qualifier | The DMARC policy ‘p’ qualifier is “none”. If the DMARC policy is neither “reject” nor “quarantine”, spoofed emails utilizing an attack technique known as SPF-bypass are likely to be accepted. See FAQs for more information. | High |
| 9 | Insecure DMARC sub-domain ‘sp’ qualifier | The DMARC policy ‘sp’ qualifier for sub-domains is set to “none”. If the DMARC policy is neither “reject” nor “quarantine”, spoofed emails from any sub-domain utilizing an attack technique known as SPF-bypass are likely to be accepted. See FAQs for more information. | High |
| 10 | Partial DMARC coverage | The DMARC “pct” value is set to less than ‘100’ (i.e., 100%), meaning the DMARC policy will only be applied to a percentage of incoming mail. A threat actor can continuously deliver spoofed emails (via SPF-bypass) until the DMARC policy isn’t applied and mail is accepted. See FAQs for more information. | Medium |
Table: Reproduced from https://caniphish.com
Scanning 1.7 million Australian Domains
Fortunately, he already had a domain list ready to go from the study he completed six months before. You should read the entire article to see how he compiled this ranking. He ended up on my target list after deduping, sanitising, and deleting names with inactive DNS servers.
Australian domains total 1.7 million.
Scaling up for DNS scanning from one to many
After some preliminary testing, he came to the conclusion that it would be impossible to extract each domain’s complete email-sender supply chain (including SPF and DMARC records) individually. It simply wouldn’t be sufficient, even with multi-threading… The problem is that he wasn’t only looking at the top layer of a domain’s SPF; rather, he was recursively searching all sub-lookups and, on average, 6 SPF records per domain.
10.2 million DNS requests in total!
He then realised that AWS Lambda functions were created specifically with this use case in mind. They enable the simultaneous execution of the identical piece of code 100s of times. The best part is that since not all functions would appear to originate from the same IP, DNS servers wouldn’t sinkhole him for making too many queries.
A Lambda function is a kind of AWS cloud computing, also known as serverless computing, that executes code very well.
Running 400 lambda functions concurrently for 24 hours
He revised the SPF & DMARC extraction script in light of this and created a lambda function to go along with it. He decided that executing 400 concurrent lambda functions in 5-minute intervals was the safest choice after some testing and research on AWS rate constraints. 15 domains would be scanned by each lambda function, and the results would be saved into a DynamoDB (NoSQL) database. He discovered that he would have to keep these Lambda functions running for 24 hours using some simple math!
What’s the impact?
The 542 domains that have implemented the “+” SPF method are all far more vulnerable to phishing-related and business email compromise attempts. Anyone with access to an email server can set one up and start sending SPF-authenticated emails under the guise of one of these domains.
While not as serious, the remaining 1,620,570 SPF and DMARC security vulnerabilities demonstrate the country’s weak adoption of email authentication and are probably representative of adoption around the world. Email receivers and secure email gateways are less able to detect the spoof in the absence of technological authentication checks.
Wrapping up
Controlling your email supply chain is essential for preventing unnecessary risks associated with email-based threats from being introduced to your company and downstream customers. You may see the complete scope of your email sender and receiver supply chains by using the free domain scan tooling developed here at CanIPhish.
Reference: https://caniphish.com/phishing-resources/blog/australian-spf-scan





