Since the end of last week, a new QBot malware campaign known as “QakNote” has been spotted in the wild. This campaign infects computers with the banking trojan utilizing malicious Microsoft OneNote’.one’ attachments.
A former banking trojan known as Qbot (QakBot) has developed into malware that is adept at gaining initial computer access. It allows threat actors to install additional malware on the infected systems and carry out data-stealing, ransomware, or other operations across the entire network.
Microsoft removed malicious macros in Office documents in July 2022. Threat actors have fewer ways to run code on targets’ computers. OneNote attachments in phishing emails have since emerged as a new attack vector to replace these macros.
Also, read Microsoft was prosecuted for open-source theft via GitHub Copilot.
Threat actors can incorporate nearly any file type, such as LNK or VBS attachments, when making malicious OneNote papers. When a user double-clicks an embedded attachment in a OneNote Notebook, they are carried out. Users must be persuaded to click on a specific location to open the embedded file. Typically accomplished using a “Double Click to View File” button or another call to action, as demonstrated below.
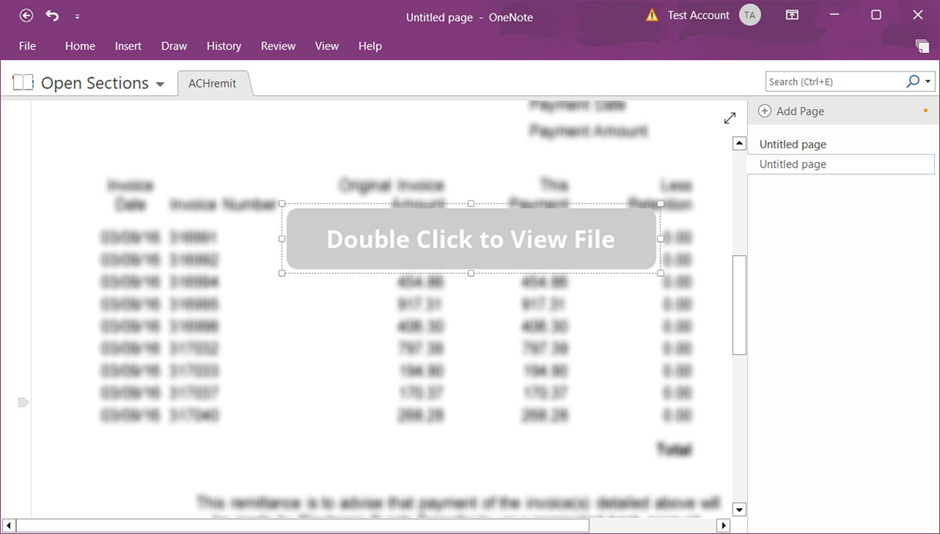
Once activated, the embedded attachments can run commands that download and install malware on the local computer.
The QakNote campaign
Security researcher Andrew Brandt reveals in a recent analysis from Sophos that since January 31, 2023. QBot’s operators have been testing this new distribution technique, using OneNote files that feature an embedded HTML application (HTA file) that downloads the QBot malware payload. Max Malyutin, a researcher at Cynet, tweeted for the first time about QBot’s distribution change on January 31, 2023.
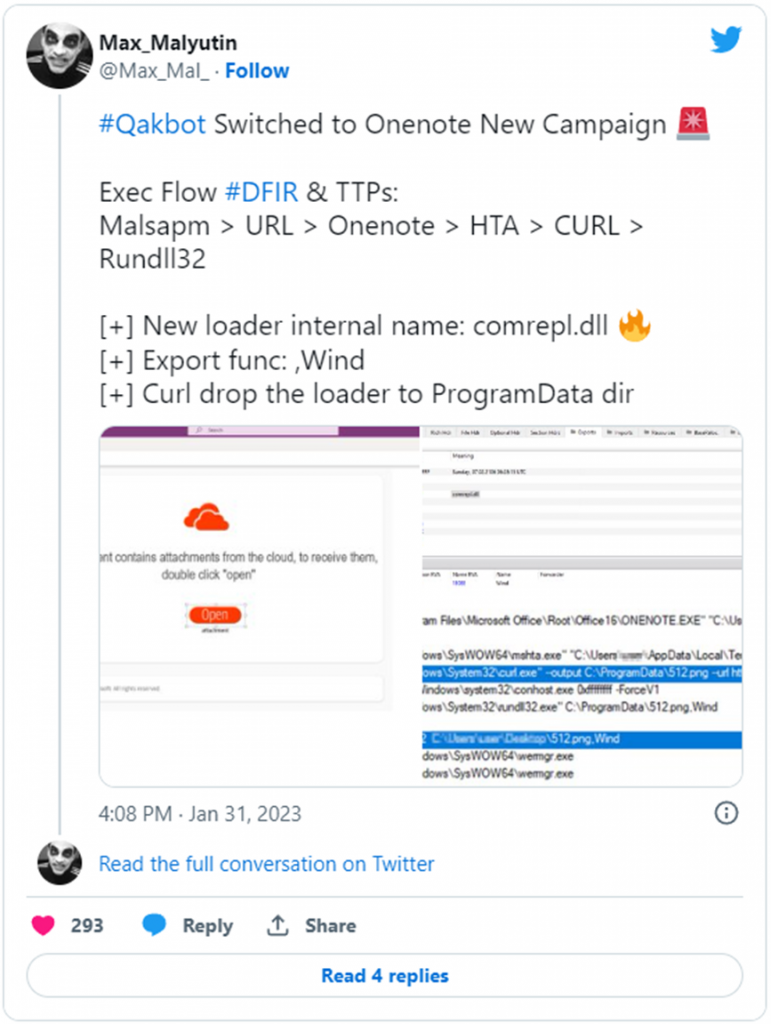
A script uses the genuine curl.exe program in the HTA file to download a DLL file (the Qbot malware) to the C:ProgramData folder, which Rundll32.exe subsequently runs.
To hide its presence and avoid detection by AV products running on the device. The QBot payload injects itself into the Windows Assistive Technology management (“AtBroker.exe”).
Also, read Anyone may start Microsoft 365 phishing attacks using the caffeine service.
According to Sophos, QBot’s operators use two distribution strategies for these HTA files: one involves sending emails with an embedded link to the weaponized.one file and the other involves “thread injections.”
With the latter, a particularly challenging tactic, the QBot operators hijack pre-existing email threads. And send its members a “reply-to-all” message with a malicious OneNote Notebook file attached. The threat actors deploy a phony button in the Notebook file that, when clicked, launches the embedded HTA attachment instead of downloading the document from the cloud, making these attacks even more deceiving for the victims.
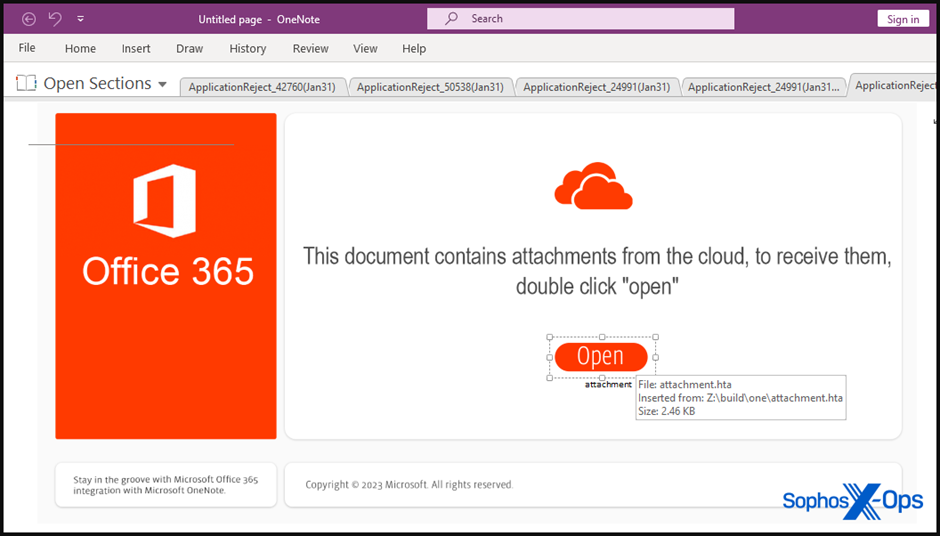
There is a probability that this activity will cause the victim to receive a warning dialogue informing them of the dangers of running attachments.
Sophos advises email administrators to think about barring all.one file extension. Because they are rarely transmitted as attachments as a safeguard against this new attack vector.





