Two ongoing surveillance operations have been discovered using Android spyware programmes to gather personal data and locate the Uyghur population in China and other countries.
This includes upgraded versions of an espionage artefact termed MOONSHINE by researchers from the University of Toronto’s Citizen Lab. In September 2019 previously unreported malware outbreak called BadBazaar.
In a detailed account of the operations, Lookout stated that “mobile surveillance tools like BadBazaar. And MOONSHINE can be used to track many of the ‘pre-criminal’ activities. The actions considered indicative of religious extremism or separatism by the authorities in Xinjiang.
The security company claims that the BadBazaar campaign began as early as late 2018. And consists of 111 distinct apps that pretend to be innocent video players, messengers, religious apps, and even TikTok.
These samples were disseminated via Uyghur-language social media websites and communication channels. But Lookout discovered a dictionary app called “Uyghur Lughat” on the Apple App Store. It connects to a server utilized by its Android equivalent to acquiring essential iPhone information.
The iOS app continues to be available on the App Store.
Android spyware
The researchers noted that since BadBazaar variants frequently obtain their surveillance capabilities by downloading updates from their [command-and-control server], it’s possible the threat actor intends to update the iOS sample in the future with a similar level of surveillance functionality.
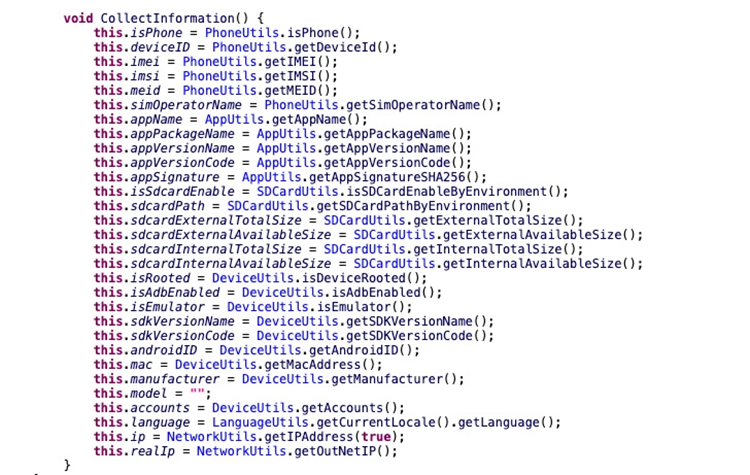
Once installed, a number of features in BadBazaar enable it to gather call logs, GPS coordinates, SMS messages, and files of interest. It can also record phone calls, take pictures, and exfiltrate a significant amount of device metadata.
Further examination of BadBazaar’s infrastructure uncovered similarities with another spyware operation targeting the racial minority that was discovered in July 2020 and used the Android toolkit DoubleAgent.
In a similar vein, MOONSHINE-based attacks have used over 50 malicious apps since July 2022. These apps are designed to record audio, download arbitrary files, and collect personal data from infected devices.
According to the researchers, most of these samples are tampered-with versions of well-known social media services like WhatsApp or Telegram. As well as tampered-with versions of Muslim cultural apps, Uyghur-language tools, or prayer apps.
A threat actor identified as POISON CARP (also known as Evil Eye or Earth Empusa), a China-based nation-state collective well-known for its attacks against Uyghurs. It has been linked to previous malicious cyber activities using the MOONSHINE Android spyware kit.
Google stated that Google Play Protect checks all Android apps before being made available on the app storefront. Also, it regularly examines app activity to look for violations of app policies.
According to the internet giant, “We regularly work with Lookout and other parties to help keep Google Play safe. The Lookout is an App Defense Alliance partner. The apps in this report were not approved by our staff in the review process. Also the apps were never made available on Google Play.
The discovery of Android spyware
The discoveries follow Check Point’s recent disclosure of information about another long-running surveillance ware operation targeting the Turkic Muslim community and using a trojan called MobileOrder since at least 2015.
According to Lookout, “BadBazaar and these new MOONSHINE variants expand the already substantial collection of distinctive surveillance are used in efforts to surveil and subsequently imprison individuals in China”.
The widespread use of BadBazaar and MOONSHINE, as well as the speed at which new functionality is being added. It shows that these families are still being developed and that there is still a need for these tools.
The finding also follows a report from Google Project Zero published last week, which found evidence of a commercial surveillance vendor using three zero-day security weaknesses in Exynos-powered Samsung phones running kernel 4.14.113 to weaponize the defects. Samsung closed the security gaps in March 2021.
However, the search engine giant claimed the hack followed a similar pattern to prior intrusions in which rogue Android apps were used to target users in Italy. And Kazakhstan with an implant known as Hermit that has been associated with an Italian business.





